 I have clocked on a few miles on my Brooks Ghost 13 shoes and I absolutely love them. I upgraded from Brooks 9 series, which previously held the rank of top running shoe in my arsenal. How could they possibly improve on the 9? I opted for the Ghost 13 over the 12 since I keep shoes for a long time and I wanted to have the most recent features. The 13 is a well-balanced shoe with neutral pronation. It feels lighter than the the 9 with the "Engineered Air Mesh" upper, it's a breathable fit. The DNA Loft is an improvement as well with a very responsive cushion, not pillow soft, but what you would expect during a run. I liked many of the colors schemes, and ultimately gave the choice to much more fashion-savvy daughter. I settled on color: 053 - Black/Grey/Stormy. The combo almost looks almost navy blueish, really sharp. From a sizing perspective, I go with a 10.5 US in a D-width. The sizing from Ghost 9 to Ghost 13 was true and accurate. I made no sizing changes between the series. Brooks is simply the best running shoe out there. Weber's decision to focus Brooks on running shoes and do it well has been impressive. I will continue to "run happy" with Brooks Ghosts.
0 Comments
 On Steve Blank's recommendation, I am reading Business Model Generation by Alexander Osterwalder and Yves Pigneur. The first thing that strikes me about this book is the visualizations it has. Definitely not a boring read! The illustrations and use of space on each page to highlight concepts are impactful. There are 9 building blocks
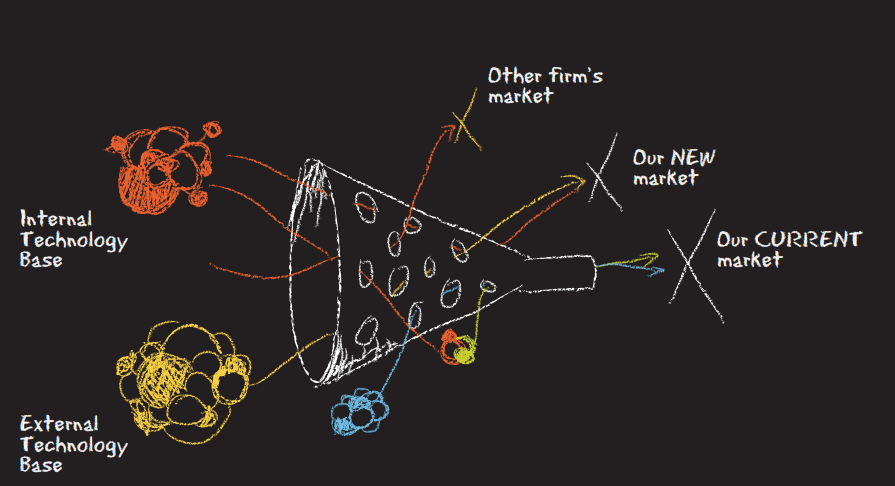
The author's highlight familiar examples such as the transformation of the book publishing industry. They cover Lego's long tail strategy of customer-designed kits, Google's business model of targeted text advertising over the global web. Also included is a freemium strategy coined by Jarid Luckin and popularized by Fred Wilson. and the Open Innovation approach (below). I found you can download the Business Model Canvas, Value Proposition Canvas, Business Portfolio Map, Team Alignment Map, and many more resources at Strategyzer.com  Jeff Daniels will be the CyberQuest keynote speaker for the second year in a row. The competition date for 2021 will be Saturday, February 6th. This year will be a virtual event. Starting in 2018, CyberQuest is a cybersecurity competition for high school students to demonstrate and improve their skills. The teams are outstanding and highly technical. We usually meet at the Fort Worth Air Force Plant 4 facility and tour the a/c assembly lines. This year, the challenges may include:
For a complete list of eligibility requirements see the Official Rules  Jeff will be joining a panel to discuss Industry 4.0, Business Impact (ROI), Ethics, Big Data and Data Analytics. Learn how data science and artificial intelligence (AI) can add value to your business or organization. In this free 3-day workshop, you will be able to interact with IBM and SUNY technical leaders in the Data Science and Artificial Intelligence profession. You will hear from SUNY and IBM experts on topics including: Industry 4.0, Business Impact (ROI), Ethics, Big Data and Data Analytics. The workshop will be split between talks and hands-on labs and each day will end with a Q&A panel session. The workshop will culminate with a panel discussion on "How to get started with AI"
 Dr. Jeff Daniels was recognized with the prestigious NOVA Award, Lockheed Martin's highest honor presented annually to individuals and teams who have made outstanding contributions to the corporation's mission and business objectives. The 26th annual NOVA Award recognizes Jeff and teammates "working tirelessly to deliver technology products and services in record time so that employees could continue working and Lockheed Martin could continue delivering on our customer commitments despite unprecedented change during the global pandemic crisis." The Lockheed Martin NOVA Awards were created in 1995. The name "NOVA" aptly describes the contributions of the winners as the bright stars of the corporation. To be considered for a NOVA award, individuals and teams must demonstrate outstanding contributions to the corporation’s mission and business objectives in the four categories of exceptional service, leadership, teamwork and technical excellence. 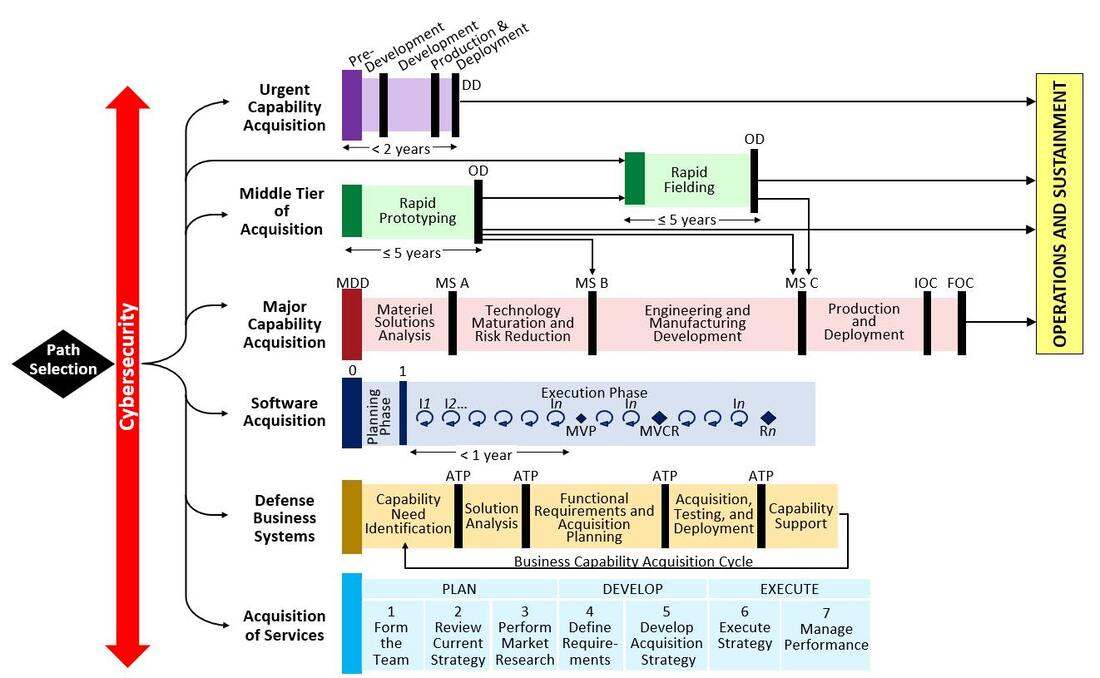 I've been participating in Steve Blank's course and thought you might enjoy this session with the Honorable Ellen Lord, the Under Secretary of Defense for Acquisition and Sustainment. She is responsible to the Secretary of Defense for acquisition; developmental testing; contract administration; logistics and materiel readiness; installations and environment; operational energy; chemical, biological, and nuclear weapons; the acquisition workforce; and the defense industrial base. It's outstanding and worth listening to. Highlights include:
Some of the readings for this week included How the DOD Acquires Weapons Systems, The Planning, Programming and Budgeting Process, Acquisition Reform in the NDAA, Defense Primer on DOD Contractors, and on the Defense Industrial Base 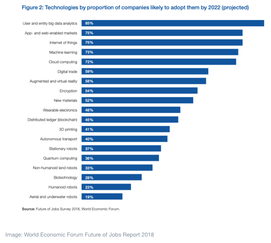 The House of Commons Science & Technology Committee produced the second report entitled Digital Skills Crisis. The report found that the "digital divide" is growing:
A 2018 World Economic Forum Future of Jobs Report estimates that that over half of all employees will require significant reskilling by 2022. The WEF states, "companies that are successful in workforce transformation will be able to harness new and emerging technologies to reach higher levels of efficiency of production and consumption, expand into new markets, and compete on new products for a global consumer base composed increasingly of digital natives.'” A 2020 study by service provider Salesforce identified similar gaps. The 2020 report entitled, "The Digital Skills Gap is Widening Fast. Here’s How to Bridge It" identifies nearly "133 million new roles generated as a result of the new division of labor between humans, machines and algorithms may emerge globally by 2022." In January, 2021, I wrote about the Atlas VPN report that found the top critical skills in cybersecurity are:
The workforce must prepare for continuous learning to stay current with digital skills. Below are several examples
 A recent study by IBM found that 95% of IT leaders surveyed said they are looking to adopt public, hybrid or private cloud strategies. This is far different that when I wrote the first dissertation on cloud computing in 2011. The literature was bearish on cloud computing with security controls being one of the biggest inhibitors of using cloud platforms. The State of IT Transformation Study conducted by the Managed Infrastructure Services unit of IBM's Global Technology Services division. Nearly a quarter of CIOs and CTOs (24%) surveyed say their company is just starting its IT modernization journey or has yet to begin modernizing. The study also found the majority of CIOs and CTOs surveyed identified the following needs:
My next post will be on Digital Transformation Skills. 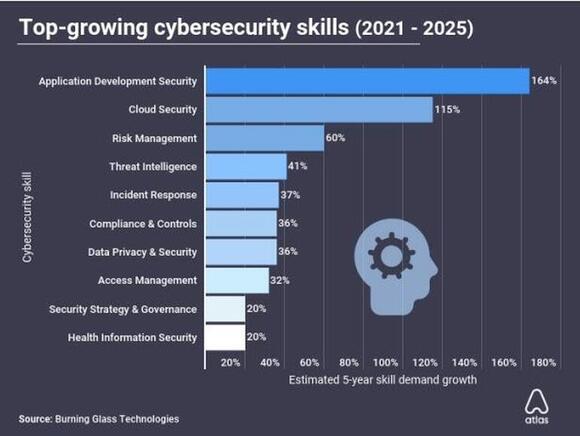 When I wrote the first doctoral dissertation on cloud computing and cybersecurity, I never imagined demand would continue to increase 10 years later! Demand for cyber professionals with the following three skills is increasing according to a report from Atlas VPN . The data is based on the report published by Burning Glass Technologies in October of 2020. The report analyzed a database of more than 1 billion historical job records and calculated 5-year growth projections for cybersecurity skills. The Top 3 skills are:
The entire Top 10 list of skills is below
I believe there is a place for business, valuation, agility for cybersecurity professionals. Perhaps this is included in the risk management section with a focus on actuarial, cost-benefit analysis, risk-reward, and cost implications of cybersecurity solutions. What do you think? -Jeff  Long range planning starts with incremental steps. One of the beautiful things about Confucius' approach is the simplicity. He asks us what our time horizon is. Once, we define this (1, 10,100 years), it becomes apparent what steps we take action on. Near-term focus, annual crop such as rice; mid-range, larger trees perhaps pecan, and finally long-term an entirely different "crop." Education is one of the keys to longevity. Active mind, problem solving, continuous learning. We must teach ourselves, our colleagues, our children. A long time horizon helps us think and act strategically. Thanks to Betsy Siwula Brandt @BetsySiwula for reminding us to Please keep teaching your children during #COVID pandemic. This is your legacy! #sundayvibes #SundayThoughts #SundayMotivation |
AuthorDirector Archives
January 2023
Categories
All
|
Photos from europeanspaceagency, ▓▒░ TORLEY ░▒▓, Lori_NY, Dean_Groom, dalecruse, Fin Cosplay & Amigurumi, Iain Farrell, erin_everlasting, palindrome6996, Easa Shamih (eEko) | P.h.o.t.o.g.r.a.p.h.y, markhillary, Matt McGee, Marc_Smith, woodleywonderworks, agustilopez, rachel_titiriga, SeaDave, cheri lucas., Caio H. Nunes, grabbingsand, Armchair Aviator, quinn.anya, Jennifer Kumar, billaday, edtechworkshop, chucknado, purpleslog, yugenro, christianeager, dground, GlasgowAmateur, expertinfantry, shixart1985 (CC BY 2.0), OiMax, Wilfried Martens Centre for European Studies, PEO, Assembled Chemical Weapons Alternatives, IBM Research, shixart1985, markus119, shixart1985, shixart1985, Wilfried Martens Centre for European Studies




 RSS Feed
RSS Feed
