 03-November, 2011Our 4-H crew went out to the extension office for an afternoon of rocket building. We built a rockets individually, then went out to the field to launch them. As the dawn set in, launch time approached. Mission control (Parker County extension agent Kayla Neill) called for all engineers and 4-Hers on deck to prepare for the launch! We had a great time building and launching the rockets. The participants learned interesting facts about space exploration. I hope we do this one again!
0 Comments
Brooks International has a good list of cloud computing events in 2012.
Top Cloud Computing Events and Conferences Events Scheduled for 2012 Cloud Expo 2012 – June 11-14- NYC – http://cloudcomputingexpo.com/ CLOUDCON 2012 – February 13-16, 2012 – Santa Clara, CA – http://www.cloudconnectevent.com/santaclara/ ICNC 2012 – January 30- February 2 – Maui, HI – http://www.conf-icnc.org/ CloudCon Expo – July 11-13, 2012 – San Francisco, CA – http://www.cloudconexpo.com/ Cloud Security Alliance Innovation Conference 2012 – January 26 – Silicon Valley, CA – https://cloudsecurityalliance.org/events/csa-innovation-conference-2012/ Cloud Identity Summit 2012 – July – Vail, CO – http://www.cloudidentitysummit.com/ IDGA 3rd Annual Cloud Computing for DoD & Government – February 21-23 – Washington DC – http://www.cloudcomputingevent.com/Event.aspx?id=619576 2012 Cloud Computing & Virtualization Conference & Expo – http://govcloudconference.com/Events/2011/Home.aspx Parallels Summit 2012 – Profit from the Cloud – February 14-16 – Orlando, FL – http://www.parallels.com/summit/2012/ Cloud Fair Conference 2012 – April 17 – 19, 2012 – Seattle, WA – http://www.cloudfairconference.com/ Cloud/Gov 2012 – February 16, Washington DC – http://www.siia.net/cloudgov/2012/ Remaining 2011 Events UP 2011 – Cloud Computing Conference – Mountain View, CA- December 5-9 – http://up-con.com/ CloudBeat2011 – November 30- December 1 – Redwood City, CA – http://venturebeat.com/events/cloudbeat2011/ CIO Cloud Summit 2011 – December 8-9 – Scottsdale, AZ – http://www.ciocloudsummit.com/ Cloud Security Alliance Congress 2011 – November 16-17 – Orlando, FL – http://www.misti.com/default.asp?page=65&Return=70&ProductID=4985&LS=cloud CloudCamp 2011 – November 19 – Chicago, IL – http://www.cloudcamp.org If you would like to add your event to our list please contact [email protected]. Source: http://blog.brooksinternational.com/top-cloud-computing-events-and-conferences/  CIO Magazine reports: Cloud computing, security and the mobile space hold the most growth potential in the coming years, according to IT professionals surveyed by tech staffing firm Modis. No kidding? Efficient (and/or affordable), secure, accessible. I don't really see anything new here. We did not need a new study to confirm these are potential growth areas. One can look at the recent and current strategic plans of the FedGov, DoD, and industry leaders to confirm. Read entire CIO article: http://www.cio.com/article/693125/Study_IT_s_Future_Lies_with_Cloud_Computing_Security_and_Mobile?source=CIONLE_nlt_insider_2011-11-07 Checked out Klout service. The idea is portray how influential one is within their network and to portray how others influence you. The data is collected through social networks and give a "score" based on the findings.
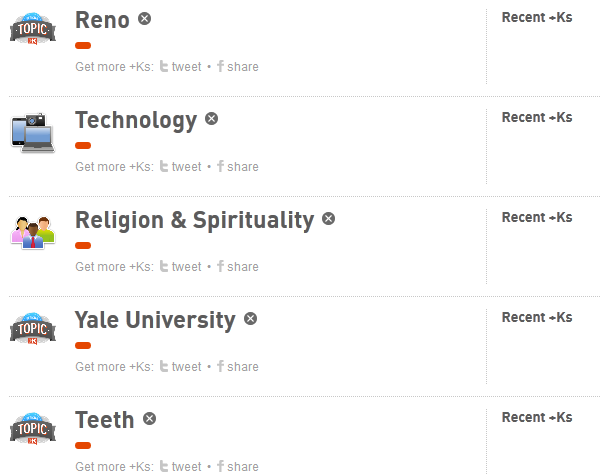
The service also identifies 5 topics one is "influential on." I consider myself well-read in some aspects of technology as well as religion and spirituality. However, I have never been to Reno nor Yale. I do not know much about teeth and orthodontology (aside from avoiding the dentist lately). I don't have much faith in klout's ability to determine if I am influential or authoritative on a topic. It's an interesting concept, but in reality, our sphere of influence is much greater than twitter and other social network mediums. Heidi Grant Halvorson, Ph.D. has a new HBR ideacast on what successful people do differently.
More at Dr. Halvorson's blog: http://blogs.hbr.org/cs/2011/02/nine_things_successful_people.html Systems Engineering is an interdisciplinary process that ensures that the customer's needs are satisfied throughout a system's entire life cycle. This process is comprised of the following seven tasks.
Source: http://www.sie.arizona.edu/sysengr/whatis/whatis.html John Roberts and Wasim Al-Hamdani presented on cloud security in the InfoSecCD '11 Proceedings of the 2011 Information Security Curriculum Development Conference.
Interesting resources in the bibliography section:
 12 Initiatives Outlined by the Comprehensive National Cybersecurity Initiative (CNCI) launched by President George W. Bush in National Security Presidential Directive 54/Homeland Security Presidential Directive 23 (NSPD-54/ HSPD-23) in January 2008.
Ariel Tseitlin and Yury Izrailevsky from Netflix share their approach to cloud adoption using "Simian Army" suite of tools.
Below are the definition of the various tools Netflix engineers created: Chaos Monkey, a tool that randomly disables our production instances to make sure we can survive this common type of failure without any customer impact. Latency Monkey induces artificial delays in our RESTful client-server communication layer to simulate service degradation and measures if upstream services respond appropriately. In addition, by making very large delays, we can simulate a node or even an entire service downtime (and test our ability to survive it) without physically bringing these instances down. This can be particularly useful when testing the fault-tolerance of a new service by simulating the failure of its dependencies, without making these dependencies unavailable to the rest of the system. Conformity Monkey finds instances that don’t adhere to best-practices and shuts them down. For example, we know that if we find instances that don’t belong to an auto-scaling group, that’s trouble waiting to happen. We shut them down to give the service owner the opportunity to re-launch them properly. Doctor Monkey taps into health checks that run on each instance as well as monitors other external signs of health (e.g. CPU load) to detect unhealthy instances. Once unhealthy instances are detected, they are removed from service and after giving the service owners time to root-cause the problem, are eventually terminated. Janitor Monkey ensures that our cloud environment is running free of clutter and waste. It searches for unused resources and disposes of them. Security Monkey is an extension of Conformity Monkey. It finds security violations or vulnerabilities, such as improperly configured AWS security groups, and terminates the offending instances. It also ensures that all our SSL and DRM certificates are valid and are not coming up for renewal. 10-18 Monkey (short for Localization-Internationalization, or l10n-i18n) detects configuration and run time problems in instances serving customers in multiple geographic regions, using different languages and character sets. Chaos Gorilla is similar to Chaos Monkey, but simulates an outage of an entire Amazon availability zone. We want to verify that our services automatically re-balance to the functional availability zones without user-visible impact or manual intervention. I like the approach of the Simian Army to simulate failures and keep systems healthy, responsive, and available. Two follow-on thoughts:
Entire post (Netflix) - http://techblog.netflix.com/2011/07/netflix-simian-army.html?m=1 |
AuthorDirector Archives
January 2023
Categories
All
|
Photos from europeanspaceagency, ▓▒░ TORLEY ░▒▓, Lori_NY, Dean_Groom, dalecruse, Fin Cosplay & Amigurumi, Iain Farrell, erin_everlasting, palindrome6996, Easa Shamih (eEko) | P.h.o.t.o.g.r.a.p.h.y, markhillary, Matt McGee, Marc_Smith, woodleywonderworks, agustilopez, rachel_titiriga, SeaDave, cheri lucas., Caio H. Nunes, grabbingsand, Armchair Aviator, quinn.anya, Jennifer Kumar, billaday, edtechworkshop, chucknado, purpleslog, yugenro, christianeager, dground, GlasgowAmateur, expertinfantry, shixart1985 (CC BY 2.0), OiMax, Wilfried Martens Centre for European Studies, PEO, Assembled Chemical Weapons Alternatives, IBM Research, shixart1985, markus119, shixart1985, shixart1985, Wilfried Martens Centre for European Studies



 RSS Feed
RSS Feed
