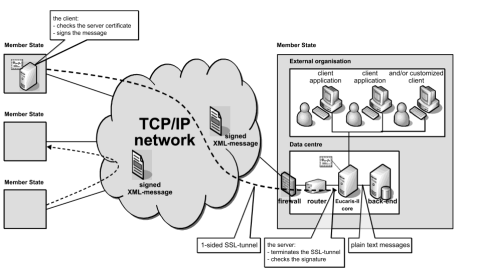
 As technologists, we need to do better. Surprisingly, the 1,246 pg UK Brexit deal includes references to Netscape 4.x, SHA-1, JPEG2000, & non-cloud infrastructure models. It's mix of outdated file standards, tools, and design practice. It's easy to dismiss the fact the authors suggest aged cybersecurity encryption algorithms and applications from the 1990's. The real question is why? The problem we are facing is much larger than a "cut and paste" error. The pace of technology is increasing, but we must bring non-technologists along with us. As professional engineers, cybersecurity scholars, cloud computing professionals, and technology practitioners, the latest standards, versions, and solution stacks are intuitive to us. They are second nature to us, we regularly apply emerging technology to solve problems. We are the creative class Richard Florida described, knowledge workers defined by Tom Peters. We use the latest package managers, version controlled repositories, and libraries in our designs, deployments, and daily builds. We design for resiliency using agile approaches with our product teams and apply DevSecOps techniques for our Software Factories. While we advocate for simple concepts like encryption at rest, encryption in transit, loosely coupled architectures, it is clear non-technologists are not processing what we are saying. How do we know this? As evidenced in the Brexit deal, we see plain text connections in the diagram, product versions from decades ago, and design patterns that will not scale. Perhaps what is most alarming is the absence of approaches such as application programming interfaces, distributed ledger technology, zero-trust concepts, identity protections, access controls, governance models. The list goes on and on. But who is to blame for these seemingly glaring omissions? Some suggest it's a cut and paste clerical error, but even at that I would expect a reviewer to question the ciphers for securing DNA profiles, fingerprint data, and vehicle registrations. The combination of SHA-1 (outdated since 2015) + Netscape (h/t Web Design Museum) + DNA profile should make us cringe. As technologists, we need to do better. Communicate differently, collaborate in new ways, share the vision with new techniques, demonstrate improved methods. I am convinced the solution, in part, lies with engineers, technologists, researchers, professors, and practitioners. I recommend the Brexit authors start with core foundational standards to design modern #cloud #architecture for #scaling & #security. There are so many helpful resources, I included 4 that focus on cloud, cloud cybersecurity, re:invent conference proceedings, and even a lab with hands-on instruction to build a distributed ledger to manage vehicle titles! In additional to the technology standards, we need to appropriately address the ethical use of the data collected. It's time for the non-technologists to treat technology as essential to security and design of systems, not merely an "after-thought." The challenge before us is to step out of our technology domain and work across boundaries to improve the way we are working, the concepts we are advocating, and created scalable, secure, safe platforms on which future communities will build. References:
0 Comments
 As we approach the close of 2020, we reflect on a year that tested our community of global leaders in health, security, and productivity like no other time in recent memory. While the past 12 months have proved to be tumultuous, volatile, and ambiguous, I would like to share some of the lessons we learned in hopes they may be applied to the following year. As we usher in 2021 with the inspiration of hope and promise, 3 leadership lessons from 2020 are apparent: technology advantage, demand for leadership, and integration of processes and platforms. Leaders who focus on these areas will successfully guide their organizations, product teams, and companies. 1. Technology Advantage
In 2020, we proved the human spirit endures. From gratitude, to humble engagement, listening with empathy, and servant leadership, we endure. Focusing on the technology advance, leadership approach, and integration, we will make a positive difference in 2021. We are seeing an increasing volatile, uncertain, complex, and ambiguous (VUCA) global environment. Countries and organizations that excel will invest in automation and integration of platforms and systems.
As technologists, we have identified 21 emerging technology trends to watch in 2021.
I just found out a new book by S Sambhi, S Sambhi, VS Bhadoria leverages my research in IoT, Distributed Ledger Technology/Blockchain, Cloud Computing, and Artificial Intelligence. I am looking forward to reviewing the final publication!
IoT-Based Optimized and Secured Ecosystem for Energy Internet: The State-of-the-Art - Internet of Things In India, the concept of smart cities and Internet of Everything is taking shape with a faster pace, so the dependence on electrical energy is increasing day by day. Renewable energy is being adopted rapidly to overcome the power shortages and to meet the power demand.  I am thrilled to join you for the Winter 2021 session of CST 620 9042 Prevention of Cyber Attack Methodologies (2211). Although we officially begin on 12 January, 2021 I wanted to simply say hi and welcome each of you :) What to expect:
Have a wonderful holiday. I hope you can enjoy some downtime before we bring on 2021! Be well, Jeff Professor, UMGC @jeffdaniels  ...The big military funding bill contains a lot of AI items… The United States is about to get a bunch of new AI legislation and government investment, thanks to a range of initiatives included in the National Defense Authorization Act (NDAA), the annual must-pass fund-the-military bill that winds its way through US politics. For those of us who lack the team to read a 4,500 page bill (yes, really), Stanford HAI has done us a favor and gone through the NDAA, pulling out the relevant AI bits. What the US military is doing about AI:
Source: James Clark AI Blog  Interesting research as the Felps et. al explore the the impact on deep neural networks and machine learning as individuals take control of their data and remove PII and personal data. Entire paper here Class Clown: Data Redaction in Machine Unlearning at Enterprise Scale Abstract: Individuals are gaining more control of their personal data through recent data privacy laws such the General Data Protection Regulation and the California Consumer Privacy Act. One aspect of these laws is the ability to request a business to delete private information, the so called “right to be forgotten” or “right to erasure”. These laws have serious financial implications for companies and organizations that train large, highly accurate deep neural networks (DNNs) using these valuable consumer data sets. However, a received redaction request poses complex technical challenges on how to comply with the law while fulfilling core business operations. We introduce a DNN model lifecycle maintenance process that establishes how to handle specific data redaction requests and minimize the need to completely retrain the model. Our process is based upon the membership inference attack as a compliance tool for every point in the training set. These attack models quantify the privacy risk of all training data points and form the basis of follow-on data redaction from an accurate deployed model; excision is implemented through incorrect label assignment within incremental model updates. Dr. Jeff Daniels, editor of the Journal of the British Blockchain Association received a Certification of Appreciation from JBBA founder, editor in chief and president Dr. Naseem Naqvi, FBB
Daniels said, "I am thankful to work with Dr. Naseem Naqvi and the editorial board at JBBA. We are doing important research at the British Blockchain Association. Dr. Naqvi and our colleagues are publishing critical research in the fields of medical, technology, cybersecurity, finance, industrial systems, and many other domains. Distributed Ledger Technology will play a pivotal role in future cybersecurity, assurance, and trusted platform solutions." The JBBA, the Journal of the British Blockchain Association, is the world’s first peer-reviewed, academic Blockchain journal that is available both in print, and online. The JBBA is a fully open access journal offering a wide-ranging and comprehensive coverage of all facets of DLT/ Blockchain Technology and Cryptocurrencies. We welcome manuscripts reporting Blockchain and DLT research projects, scientific methods, case studies, analysis, reviews and practical use cases of emerging distributed ledger technologies and innovations including sound descriptive work. All research articles undergo a fully ‘double-blind’ peer review process by 2-3 independent, external reviewers. The publication can be found at https://jbba.scholasticahq.com/ I am partnering with Kelly Caudle, Program head of Cisco Academy Support Center (ASC), Instructor Training Center, VMWare Academy, IT Academy, and Lead Instructor on a grant for Cisco Training.
We will start in February 2021, thankful for the partnership! |
AuthorDirector Archives
January 2023
Categories
All
|
Photos from europeanspaceagency, ▓▒░ TORLEY ░▒▓, Lori_NY, Dean_Groom, dalecruse, Fin Cosplay & Amigurumi, Iain Farrell, erin_everlasting, palindrome6996, Easa Shamih (eEko) | P.h.o.t.o.g.r.a.p.h.y, markhillary, Matt McGee, Marc_Smith, woodleywonderworks, agustilopez, rachel_titiriga, SeaDave, cheri lucas., Caio H. Nunes, grabbingsand, Armchair Aviator, quinn.anya, Jennifer Kumar, billaday, edtechworkshop, chucknado, purpleslog, yugenro, christianeager, dground, GlasgowAmateur, expertinfantry, shixart1985 (CC BY 2.0), OiMax, Wilfried Martens Centre for European Studies, PEO, Assembled Chemical Weapons Alternatives, IBM Research, shixart1985, markus119, shixart1985, shixart1985, Wilfried Martens Centre for European Studies







 RSS Feed
RSS Feed
