|
John Roberts and Wasim Al-Hamdani presented on cloud security in the InfoSecCD '11 Proceedings of the 2011 Information Security Curriculum Development Conference.
Interesting resources in the bibliography section:
16 Comments
 12 Initiatives Outlined by the Comprehensive National Cybersecurity Initiative (CNCI) launched by President George W. Bush in National Security Presidential Directive 54/Homeland Security Presidential Directive 23 (NSPD-54/ HSPD-23) in January 2008.
CIO shares Gartner VP Ken McGee's 16 long-held business practices that need to be discontinued:
The short list of targeted items includes: 1. Stop recommending mega projects 2. Eliminate differences between CIO/CEO projects 3. Terminate projects that do not improve the income statement 4. Abandon CIO priorities that don't support CEO priorities 5. Stop recommending mega projects 6. Terminate existing apps that do not yield measurable business value 7. End the practice of putting the enterprise IT spending within the CIO budget 8. Abolish environment of little or no IT spending accountability 9. Eliminate IT caused business model disruption surprises 10. Kill cloud-a-phobia 11. Abandon level 1,2,3 tech support 12. Kill chargeback systems 13. Stop issuing competitive bids 14. Stop holding onto unfunded projects. Stop IT hoarders 15. End discrimination against behavioral skills around social sciences 16. End unbalanced support between back and front office http://www.cio.com/article/692130/Gartner_16_Long_Held_IT_Business_Practices_You_Need_to_Kill The Fort Worth Alliance Airshow was cancelled on 23 October, 2011 due to weather conditions. The weather on Sunday was fantastic, but the parking lot was soaked. The muddy mess led to the cancellation of all performances due to unsafe conditions.
The Alliance Airshow staff does a great job planning for the event. I've been in attendance many years at the Captain's club, Flight Deck, and met many of my friends and colleagues in Fort Worth. The vendors, performers, and attendees wanted the show to go on. As pilot Michael Rambo puts it, "just like flying, safety first." See you next year! One of my favorites from the 2006 Alliance Airshow: One of my colleagues, Dr. Van Dewark is looking for a new moppin sauce recipe. The one below is real good for pork...especially if you like
Deejay’s Infamous Dipping Sauce For Pulled Pork 2-juiced lemons, 1 teaspoon white pepper, 1 teaspoon sea salt, 1 teaspoon Cajun spice, 4 teaspoons pure Maple syrup, 4 teaspoons Tomato Based BBQ sauce Some great guides that have helped me smoke meats, create rub recipes, etc: http://www.deejayssmokepit.net Ariel Tseitlin and Yury Izrailevsky from Netflix share their approach to cloud adoption using "Simian Army" suite of tools.
Below are the definition of the various tools Netflix engineers created: Chaos Monkey, a tool that randomly disables our production instances to make sure we can survive this common type of failure without any customer impact. Latency Monkey induces artificial delays in our RESTful client-server communication layer to simulate service degradation and measures if upstream services respond appropriately. In addition, by making very large delays, we can simulate a node or even an entire service downtime (and test our ability to survive it) without physically bringing these instances down. This can be particularly useful when testing the fault-tolerance of a new service by simulating the failure of its dependencies, without making these dependencies unavailable to the rest of the system. Conformity Monkey finds instances that don’t adhere to best-practices and shuts them down. For example, we know that if we find instances that don’t belong to an auto-scaling group, that’s trouble waiting to happen. We shut them down to give the service owner the opportunity to re-launch them properly. Doctor Monkey taps into health checks that run on each instance as well as monitors other external signs of health (e.g. CPU load) to detect unhealthy instances. Once unhealthy instances are detected, they are removed from service and after giving the service owners time to root-cause the problem, are eventually terminated. Janitor Monkey ensures that our cloud environment is running free of clutter and waste. It searches for unused resources and disposes of them. Security Monkey is an extension of Conformity Monkey. It finds security violations or vulnerabilities, such as improperly configured AWS security groups, and terminates the offending instances. It also ensures that all our SSL and DRM certificates are valid and are not coming up for renewal. 10-18 Monkey (short for Localization-Internationalization, or l10n-i18n) detects configuration and run time problems in instances serving customers in multiple geographic regions, using different languages and character sets. Chaos Gorilla is similar to Chaos Monkey, but simulates an outage of an entire Amazon availability zone. We want to verify that our services automatically re-balance to the functional availability zones without user-visible impact or manual intervention. I like the approach of the Simian Army to simulate failures and keep systems healthy, responsive, and available. Two follow-on thoughts:
Entire post (Netflix) - http://techblog.netflix.com/2011/07/netflix-simian-army.html?m=1 American test pilot Chuck Yeager flew the X-1 aircraft, affectionately named "Glamorous Glennis" after his wife on October 14th, 1947. Yeager's historic flight signaled the first manned flight to break the sound barrier, launching the USA flight program ahead of Britain and Germany.
It was more rocket than plane, developed specifically to fly through the shock waves of the sound barrier, with Yeager as pilot. "About half of the engineers gave us no chance at all of ever successfully flying beyond the speed of sound. They said it's a so-called barrier and the airplane would go out of control or disintegrate, but I didn't look at it that way." More info @ http://www.youtube.com/watch?v=dke2i-xO1uo Excerpt from Andy Gravvet's 08-Sept article on GovLoop
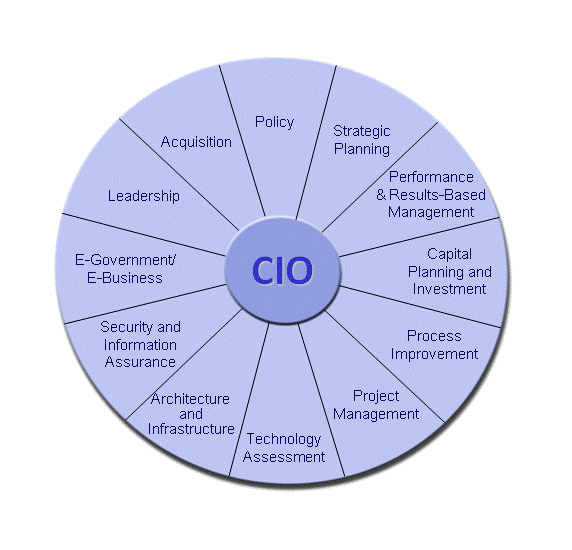
Chief Information Officer's Role The primary role of the CIO is to provide policy direction, maintain the IT infrastructure of the organization, ensure proper security measures are followed, and to evaluate and control capital expenditures to facilitate the portfolio management of the organization. The graphic below illustrates a more detailed list of the functions of the CIO. Clinger-Cohen defines the general responsibilities as follows: "(1) providing advice and other assistance to the head of the executive agency and other senior management personnel of the executive agency to ensure that information technology is acquired and information resources are managed for the executive agency in a manner that implements the policies and procedures of this division, consistent with chapter 35 of title 44, United States Code, and the priorities established by the head of the executive agency; (2) developing, maintaining, and facilitating the implementation of a sound and integrated information technology architecture for the executive agency; and (3) promoting the effective and efficient design and operation of all major information resources management processes for the executive agency, including improvements to work processes of the executive agency." Chief Technology Officer's Role The CTO's responsibility is to provide overall awareness of technologies that can be used to advance the mission of the organization. This role is illustrated in the graphic below and the primary functions of the CTO are described below:
Russell Working over @ Ragan.com shares his techniques before responding to those snarky emails.
Instead of a scorched earth policy, try these tips to avoid a "reply-all firefight":
Conventional wisdom holds "do not argue with an idiot, people watching [reading] may not be able to tell the difference." Sound advice for limiting a CLM (career limiting move) via email. Have a great day |
AuthorDirector Archives
January 2023
Categories
All
|
Photos from europeanspaceagency, ▓▒░ TORLEY ░▒▓, Lori_NY, Dean_Groom, dalecruse, Fin Cosplay & Amigurumi, Iain Farrell, erin_everlasting, palindrome6996, Easa Shamih (eEko) | P.h.o.t.o.g.r.a.p.h.y, markhillary, Matt McGee, Marc_Smith, woodleywonderworks, agustilopez, rachel_titiriga, SeaDave, cheri lucas., Caio H. Nunes, grabbingsand, Armchair Aviator, quinn.anya, Jennifer Kumar, billaday, edtechworkshop, chucknado, purpleslog, yugenro, christianeager, dground, GlasgowAmateur, expertinfantry, shixart1985 (CC BY 2.0), OiMax, Wilfried Martens Centre for European Studies, PEO, Assembled Chemical Weapons Alternatives, IBM Research, shixart1985, markus119, shixart1985, shixart1985, Wilfried Martens Centre for European Studies




 RSS Feed
RSS Feed
